Date: 25.09.2022 - Category: Tutorial
Learn Nmap to find your first Network Vulnerability
Learn how to use Nmap, to scan and analyze your network, to find network vulnerabilities. Perform Version and OS detection easily and find open ports.
Nmap Cheatsheet -
Official Website -
GitHub
What is Nmap?
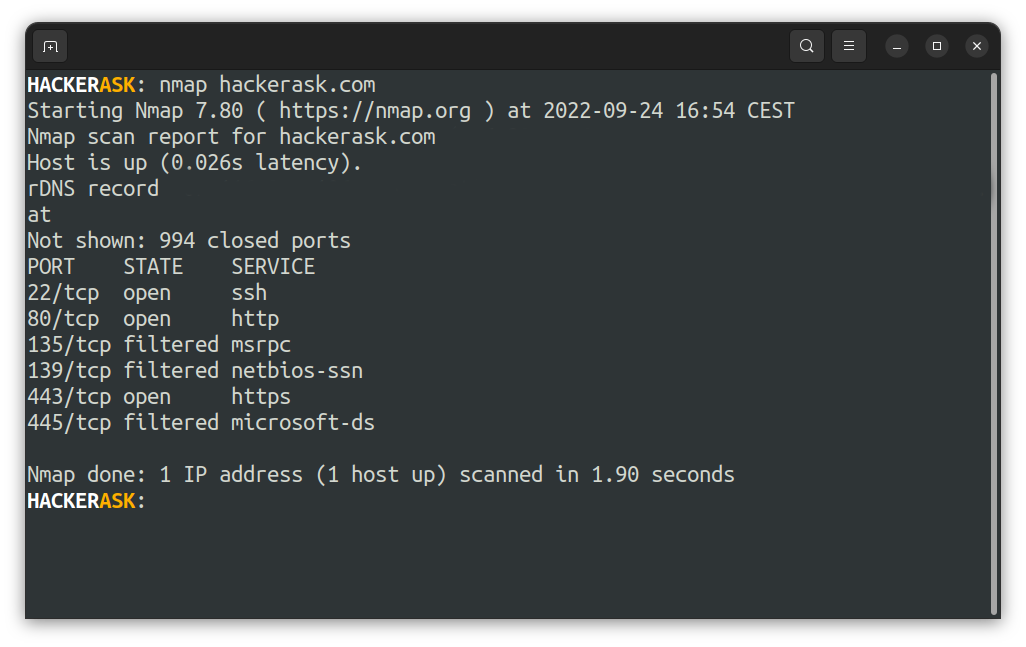
Network Mapper, alias Nmap, is an open-source tool for network exploration and security auditing. You can use it to scan large networks pretty fast, but it also works against single hosts. Nmap sends raw IP packets to the target host to gather information and output the list of the scanned hosts. It will determine what services, operating systems, packet filters/firewalls, and dozens of other stuff are running on the scanned system.
Commands
Basic Scanning
To create a map of the target network, you have to scan it to list all active devices. To do that, you can use two different techniques:
- Ping scan - Scans all running devices in a subnet:
- Host scan - Scan a single host for the 1024 well-known ports:
 To target a single or range of ports you can use the
To target a single or range of ports you can use the -p flag:
- Scan a single port:
- Scan a range of ports:
- Scan a list of ports:
- Scan all ports:
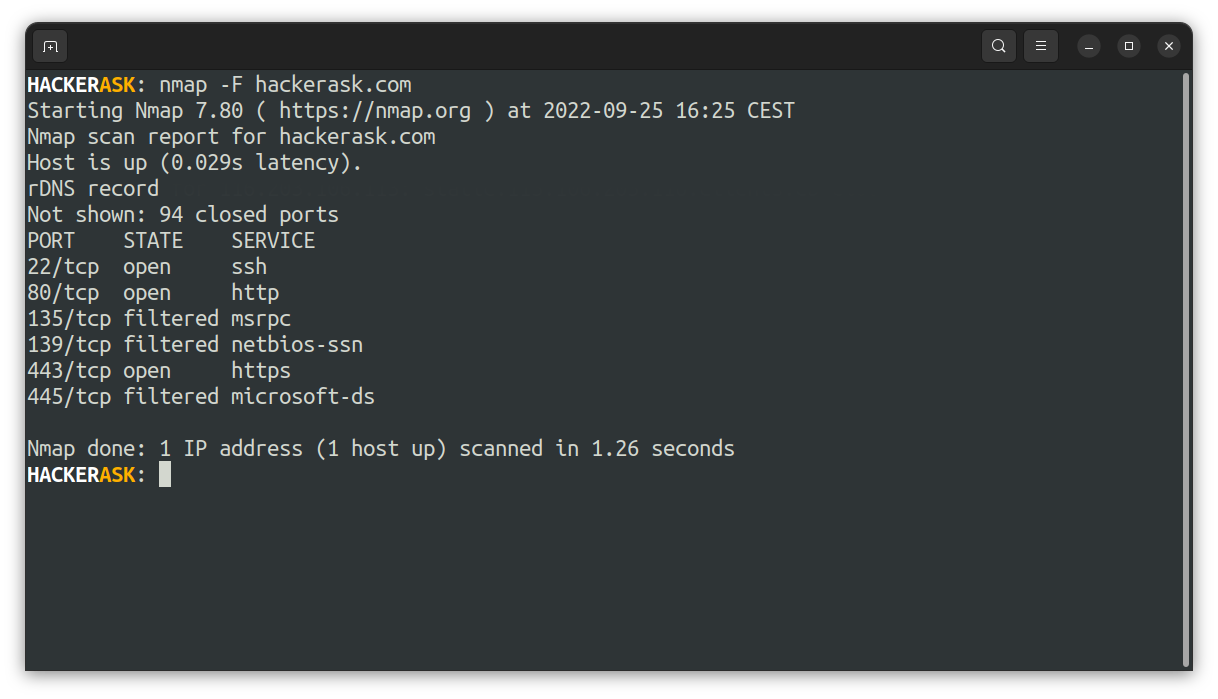
- Scan the 100 most popular ports using the
-Fflag:
 To get more information about the scanned host, you can use the verbose output flag
To get more information about the scanned host, you can use the verbose output flag -v:
That is useful to export nmap results to avoid redundant scans and monitor the step by step actions Nmap performs on a network.
Stealth Scanning
Stealth scans complicate the detection of the scanning system for a target by not completing the 3-way handshake of a TCP connection.
It sends an SYN packet to the host. If an SYN/ACK packet is received, a port on the target is open, and you can open a TCP connection.
To perform a stealth scan, you have to use the flag -sS:
The downside of stealth scanning is that it is slower and not as aggressive as the other types of scanning.
Version Scanning
Let's find the versions of applications with Nmap, which is a crucial part of penetration testing.
You can search for existing vulnerabilities in the Common Vulnerability and Exploits (CVE) database for the particular found version.
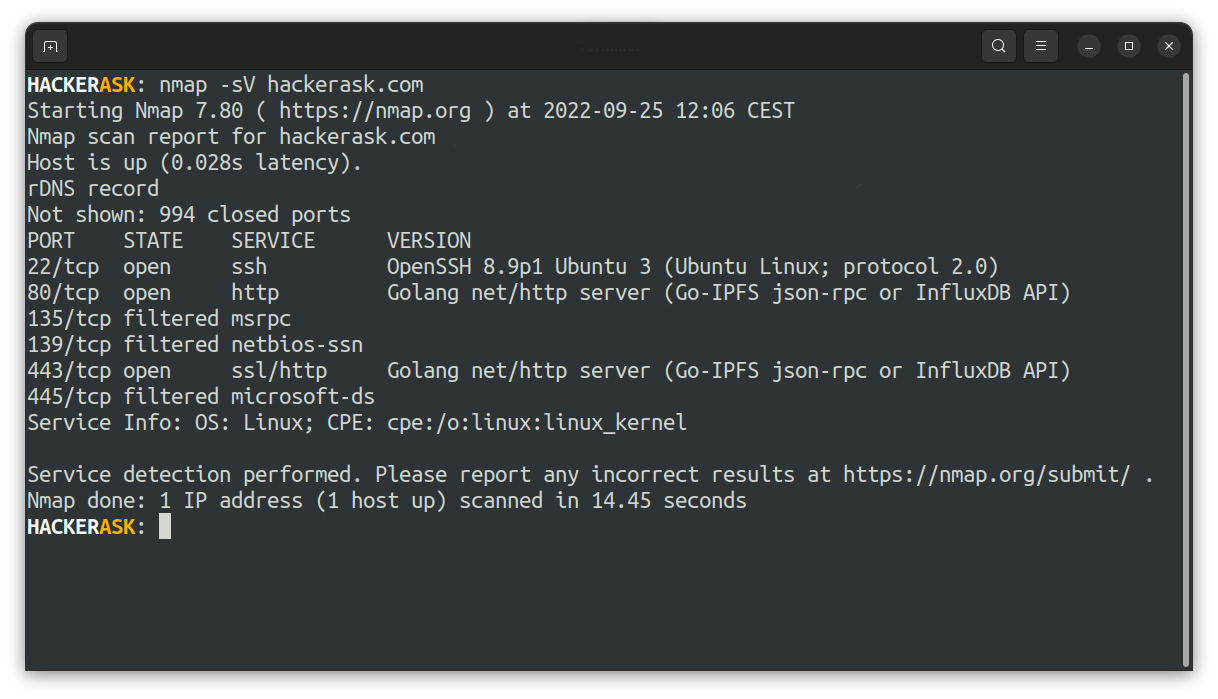
To scan a version of a service you can use the -sV flag:
But keep in mind, that the version scan is not always correct. But it will give you a good overview of the services on the scanned system.
Operating System Scanning
Nmap can also provide information about the active operating system on the target host using TCP/IP fingerprints.
You can use the -O flag to enable the operating system detection:
It is also possible to use the flag -osscan-limit to limit the detection to promising targets. Nmap will show the probability of each operating system guess.
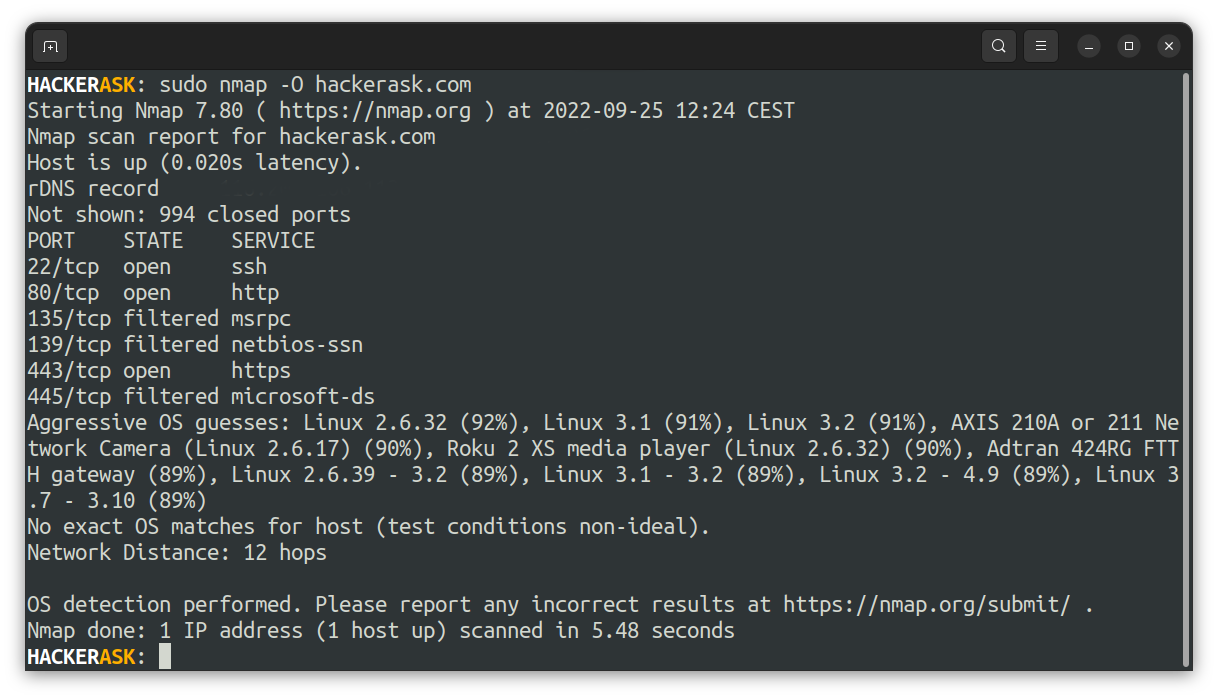 Like version scanning, the OS scan is not always accurate but can help to collect some information about the target.
Like version scanning, the OS scan is not always accurate but can help to collect some information about the target.
Aggressive Scanning
But to get far better information than with regular scans, Nmap provides an aggressive mode. That enables OS and version detection, traceroute and script scanning.
The flag -A will enable the aggressive scan:
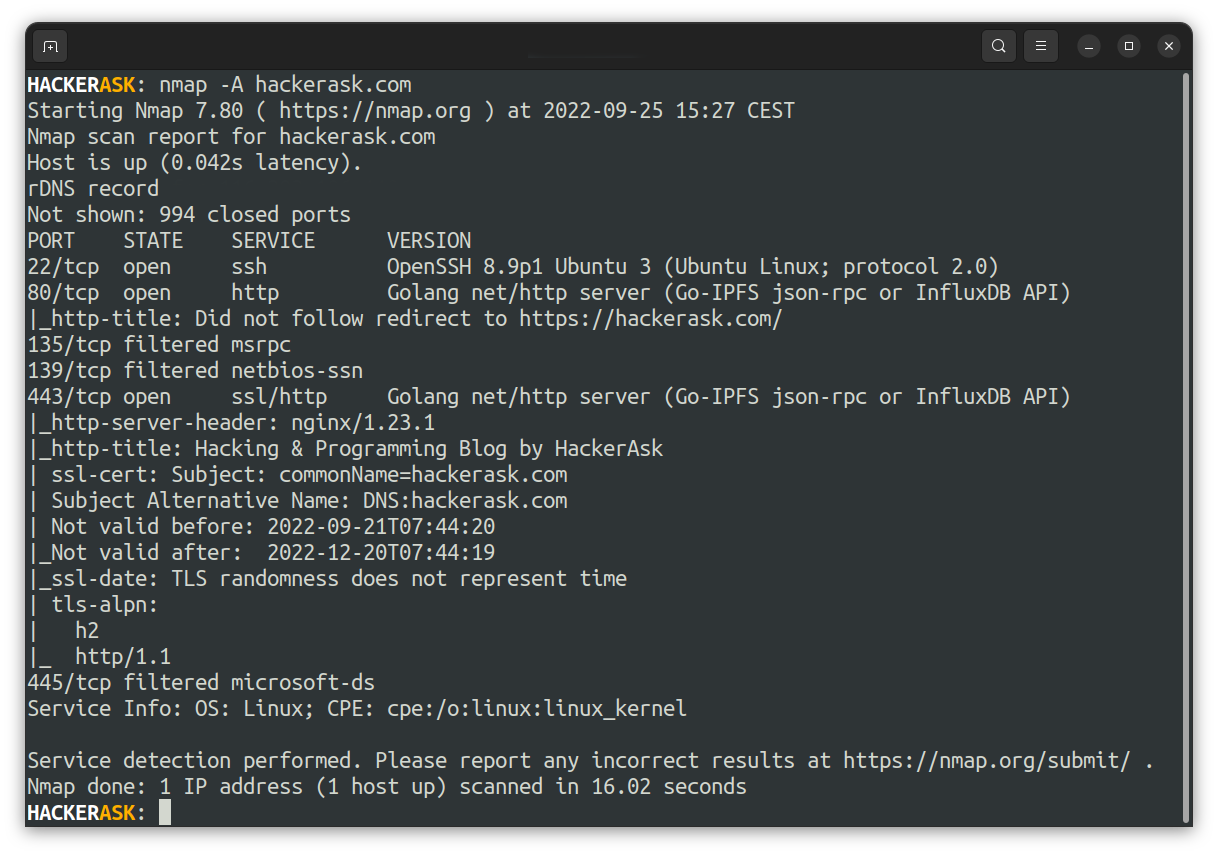 However, aggressive scans will send more packets to the target host, which is easier detectable.
However, aggressive scans will send more packets to the target host, which is easier detectable.
Nmap Scripting Engine
The Nmap Scripting Engine(short NSE) is a powerful tool write and automate scans.
How to perform a scan using the NSE
To perform such a scan use the --script flag:
How to find NSE scripts?
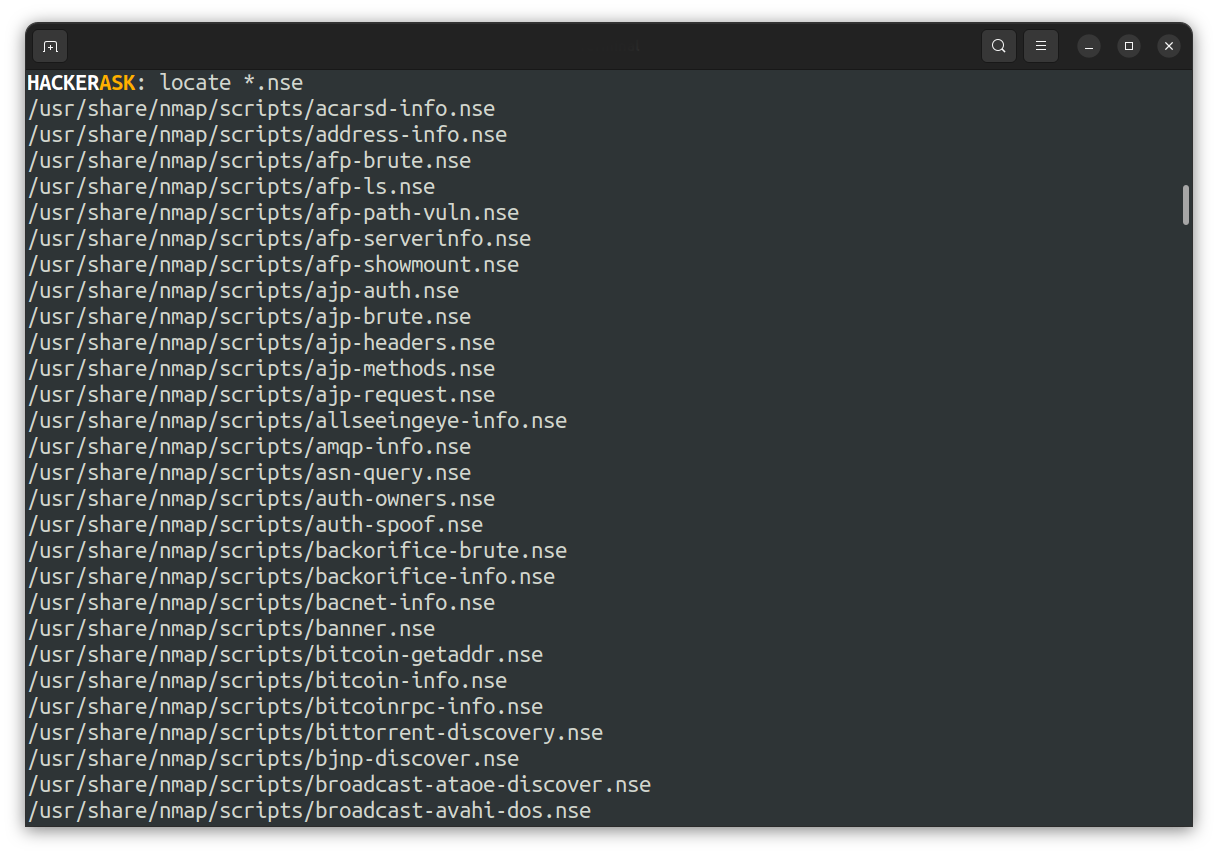
You can find the location of all available NSE scripts using the locate util:
 You can also use the list of NSE scripts on the nmap homepage:
You can also use the list of NSE scripts on the nmap homepage:
List of Nmap Scripts
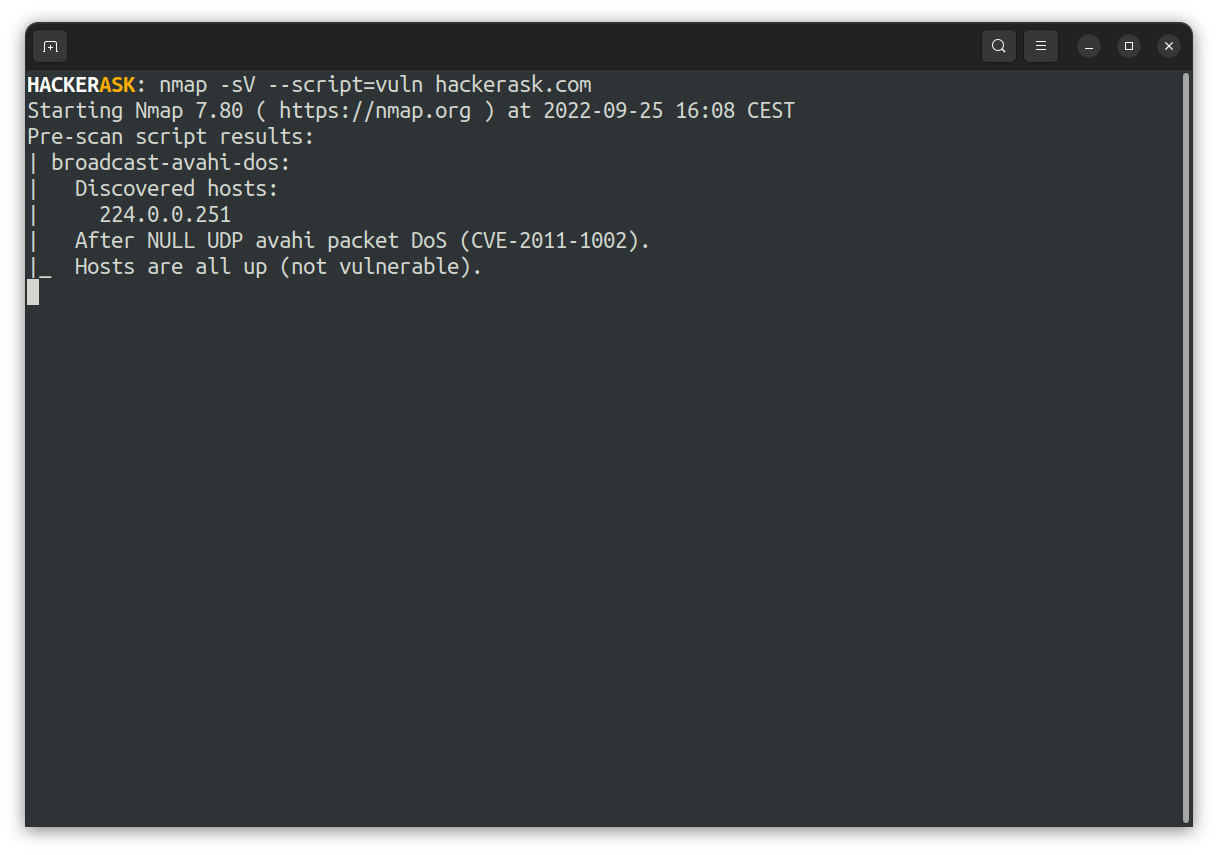
How to use Nmap to scan for Vulnerabilities
To peform a vulnerability scan, Nmap provides the powerful script category vuln. To allow Nmap to use the Vulners exploit database, pass the -sV flag while using the NSE script: